This page explains what rtptunnel is and how it works.
Gphone or Gnome-O-Phone is an internet telephone program for Linux written by Roland Dreier. Please visit the official homepage of gphone to learn more about it. The following figures illustrate how gphone transmits information over the net. There is no information about soundcards, mikes, and speakers here, since that is in not the focus of this page.
Normal gphone operation
Gphone behind a firewall (4 machines)
A 3-machine setup
A 2-machine setup
 |
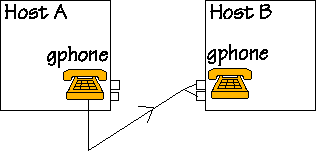
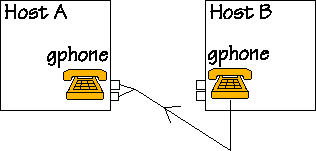
For using gphone you need two computers connected to the net. The two small boxes on each computer represent the RTP ports allocated for receiving audio and control information. This is exclusive allocation, that is once gphone allocated them, no other program can allocate them again until gphone stops. Since RTP is defined over UDP, gphone sends and receives UDP packets. |
| | |
 |
When someone talks to the mike connected to Host A, audio and control information travels on the net on the way shown by this figure. |
 |
When someone talks to the mike connected to Host B, audio and control information travels on the net on the way shown by this figure. |
You can specify the port numbers gphone listens to and sends information to. For the gphone running on Host A, you should specify the following options:
Since gphone uses UDP packets to communicate, it is hard to talk to someone behind a firewall. To work around this problem, Roland wrote rtptunnel.
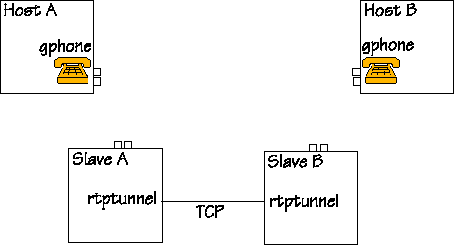 |
The figure shows a setup with four machines. People are sitting at Hosts A and B, and they are keen on talking to each other on the gphone. The computers Slave A and B are running rtptunnel that has the task of tunneling those RTP packets (UDP) through a TCP tunnel. The tunnel is already there, and it is now waiting for packets to tunnel. The figure does not show the firewall, since the system works regardless of the presence of a firewall, however, if there is a firewall, it should be between the machines Slave A and Slave B. |
| | |
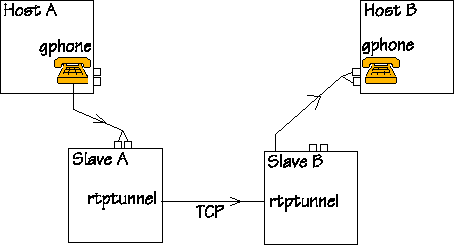 |
When someone talks to the mike connected to Host A, audio and
control information travels on the net on the way shown by this
figure:
|
| | |
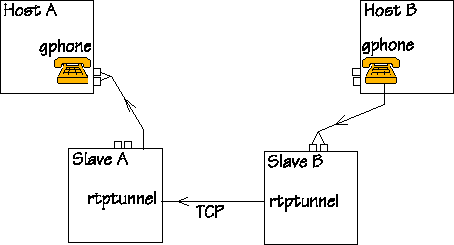 |
When someone talks to the mike connected to Host B, audio and
control information travels on the net on the way shown by this
figure:
|
With this 4 machine setup, there is no need to change any of the
default ports used by gphone or by rtptunnel. Suppose that, for
this example, the hostnames of the four computers are
hosta, slavea, hostb and
slaveb.
For this setup, you need to launch the following program on Host A:
gphone -c slavea
and on Slave A:
rtptunnel -s hosta
Rtptunnel sends and recieves at port number 5004, which is the port number gphone uses. This is possible because rtptunnel and gphone are running on separate hosts.
For Host B, you need to run:
gphone
and on Slave A:
rtptunnel -s hostb -c slavea
It is possible on Linux to run multiple programs at a time (surprise, surprise ;-)). In consequence, gphone and rtptunnel can be run on one machine.
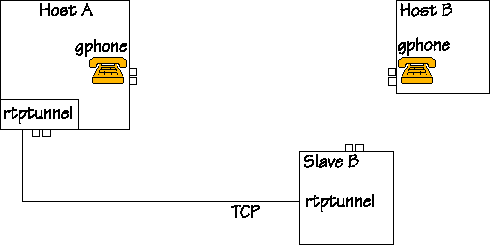 |
The figure shows a setup with three machines. People are sitting at Hosts A and B, and they are keen on talking to each other on the gphone. The computers Host A and Slave B are running rtptunnel. The tunnel is already there, and it is now waiting for packets to tunnel. The figure does not show the firewall, since the system works regardless of the presence of a firewall, however, if there is a firewall, it should be between the machines Host A and Slave B. |
| | |
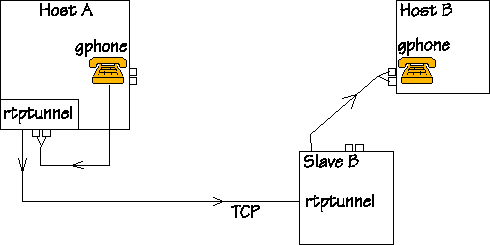 |
When someone talks to the mike connected to Host A, audio and
control information travels on the net on the way shown by this
figure:
|
| | |
 |
When someone talks to the mike connected to Host B, audio and
control information travels on the net on the way shown by this
figure:
|
Yes, now we proceed to the most complicated setup, where 2 hosts are running 4 programs.
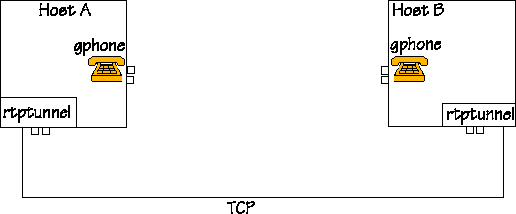 |
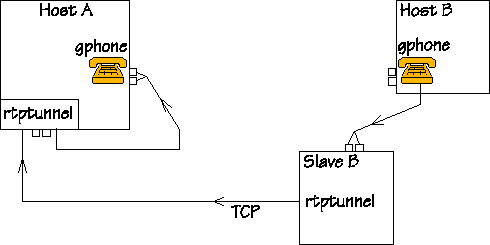
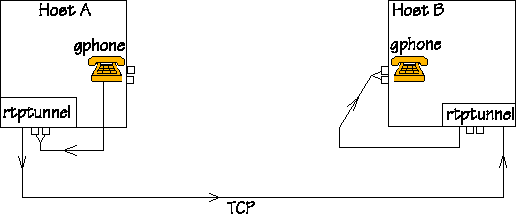
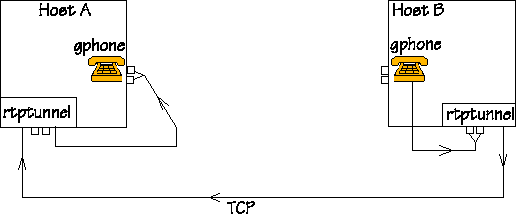
The figure shows a setup with two machines. People are sitting at Hosts A and B, and they are keen on talking to each other on the gphone. Their computers are also running rtptunnel. The tunnel is already there, and it is now waiting for packets to tunnel. The figure does not show the firewall, since the system works regardless of the presence of a firewall, however, if there is a firewall, it should be between the machines Host A and Host B. ;-) |
| | |
 |
When someone talks to the mike connected to Host A, audio and
control information travels on the net on the way shown by this
figure:
|
| | |
 |
When someone talks to the mike connected to Host B, audio and
control information travels on the net on the way shown by this
figure:
|
In order to get this configuration to work, you need 4 port numbers on both machines. This is so, because both gphone and rtptunnel need their exclusive ports to receive audio and control information.
Let's suppose for the sake of the example, that for Host A, you picked
port number 5004 for gphone to listen to, and port number 5010 for
rtptunnel to listen to. For Host B, you picked port number 5014 for
gphone to listen to, and port number 5020 for rtptunnel to listen
to. All the former port numbers are UDP port numbers and you go for
the default TCP port number. The host name of Host A is
hosta and the host name of Host B is hostb.
For this setup, you need to launch the following programs on Host A:
rtptunnel -s 5004 -r 5010
gphone -l 5004 -r 5010 -c hosta
Rtptunnel sends to port number 5004, which is the port number gphone listens to. Rtptunnel receives on port number 5010, which is the port number gphone sends to. For gphone it appears, that it talks to someone sitting at the same machine.
On Host B, you need to launch the following programs:
rtptunnel -s 5014 -r 5020 -c hosta
gphone -l 5014 -r 5020 -c hostb
Written by Ivan Szanto on
25th November, 1999
Modified by Roland Dreier on 4th December, 1999